Linux Forensics
Pentester Academy TV |
7 videos |
Updated 6 years ago
Linux Forensics
Full course description: bit.ly/nm9P7e
Course stats: 106 videos, 12 hours of content.
Linux Forensics will familiarize students with all aspects of Linux forensics. By the end of this course students will be able to perform live analysis, capture volatile data, make images of media, analyze filesystems, analyze network traffic, analyze files, perform memory analysis, and analyze malware all on a Linux system with readily available free and open source tools. Students will also gain an in-depth understanding of how Linux works under the covers.
A non-exhaustive list of topics to be covered includes:
* Live response
- First talk to the humans
- Mount response kit with known good tools
- Using netcat to minimize contamination
- Collecting volatile data
- Collecting data to determine if dead analysis is justified
- Dumping RAM
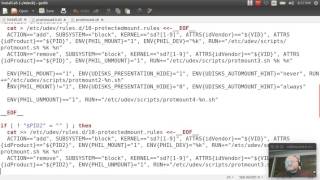
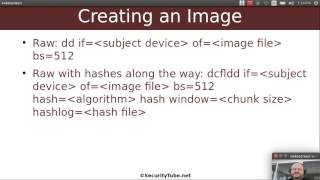
* Acquiring filesystem images
- Using dd
- Using dcfldd
- Write blocking options
* Analyzing filesystem images
- Mounting images
- Leveraging The Sleuth Kit (TSK) and Autopsy
* Timeline Analysis
- When was system installed, upgraded, booted, etc.
- Newly created files (malware)
- Changed files (trojans)
- Files in the wrong place (exfiltration)
* Digging deeper into Linux filesystems
- Disk editors
- ExtX
* Network forensics
- Using snort on packet captures
- Using tcpstat
- Separating conversations with tcpflow
- Tracing backdoors with tcpflow
* File forensics
- Using file signatures
- Searching through swap space
- Web browsing reconstruction
- Unknown files
* Memory Forensics
- Volatility Profiles
- Retrieving process information
- Recovering command line arguments
- Rebuilding environment variables
- Listing open files
- Retrieving bash information
- Reconstructing network artifacts
- Kernel information
- Volatile file system information
- Detecting user mode rootkits
- Detecting kernel rootkits
* Reversing Linux Malware
- Digging deeper into ELF
- Command line analysis tools
- Running malware (carefully)
* Writing the reports
- Autopsy
- Dradis
- OpenOffice