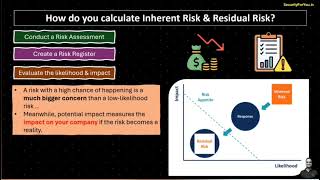
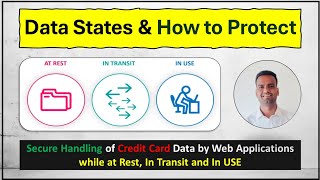
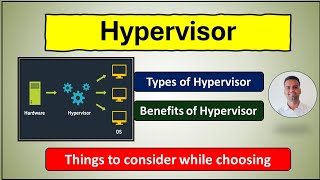
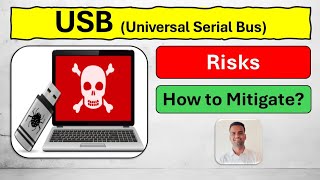
Security Professional | CISA | CRISC
Certified Information System Auditor - CISA qualified
Certified in Risk and Information System Control - CRISC qualified
ISO/IEC ISMS - Information Security Risk Management implementation and coordination with cross functional for their status.
Governance, Risk and Compliances tracking.
Conducting Internal audit of applicable controls.
Periodically reviewing effective controls and vulnerabilities.
Implementation of ISMS. Third party risk management.
Talks about #security, #leadership, #securityaudits, #securitymanagement, and #businesscontinuityplanning
Shared 9 hours ago
5 views
Shared 1 week ago
34 views
Shared 2 weeks ago
22 views
Shared 2 weeks ago
58 views
Shared 3 weeks ago
225 views
Shared 4 weeks ago
86 views
Shared 4 weeks ago
58 views
Encrypt & Decrypt USB drive using windows BitLocker | Type of encryption used & Step by step guide 💥
Shared 4 weeks ago
522 views
Shared 5 months ago
144 views
Shared 6 months ago
83 views
Shared 7 months ago
270 views
Shared 7 months ago
96 views
Shared 7 months ago
308 views
Shared 8 months ago
117 views
Shared 8 months ago
136 views
Shared 8 months ago
105 views
Shared 8 months ago
145 views
Shared 8 months ago
101 views
Why Passwords are stored as Hash & not Encrypted? Why Hashing + Salting is secure than Encryption? 💥
Shared 8 months ago
325 views
Shared 8 months ago
83 views
Shared 8 months ago
32 views
Shared 8 months ago
152 views
Shared 8 months ago
62 views
Shared 8 months ago
211 views
Shared 8 months ago
126 views
Shared 8 months ago
317 views
Shared 8 months ago
288 views
Shared 8 months ago
129 views
Shared 9 months ago
331 views
Shared 9 months ago
63 views
Shared 9 months ago
20 views
Virtual Machines - How they are transforming power of Computing? Why should you use VMs? Explained 💥
Shared 9 months ago
28 views
Shared 9 months ago
167 views
Shared 9 months ago
94 views
Shared 9 months ago
146 views
Cloud Computing and Cloud deployment models | Factors & Risks to keep in mind? Everything explained💥
Shared 9 months ago
96 views
Shared 9 months ago
369 views
How to conduct an Audit? Detailed step by step guide 💥 Different Audit phases explained wid examples
Shared 9 months ago
148 views
Shared 9 months ago
230 views
Shared 9 months ago
332 views
Shared 9 months ago
200 views
Shared 9 months ago
106 views
Shared 9 months ago
228 views
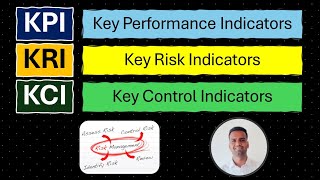
KRI vs KPI vs KCI 💥 Relationship b/w Key Performance, Risk & Control Indicators with examples solved
Shared 9 months ago
2.2K views
Shared 9 months ago
1.6K views
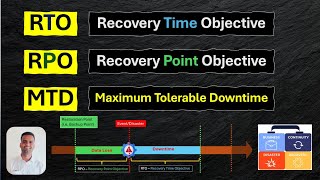
RPO, RTO & MTD in Business Continuity & Disaster Recovery | Explained in details with real examples💥
Shared 9 months ago
5.5K views
Information & Data Classification Policy 💥 Why it impotant? Different Categories of Classification 👇
Shared 9 months ago
292 views
Shared 9 months ago
103 views
Why Digital Signatures are more secure than Electronic Signature? Similarities & Differences in two👇
Shared 10 months ago
75 views
Shared 10 months ago
500 views
What is Geofence? How does it work? How Geofencing Revolutionizes Marketing using Virtual Boundaries
Shared 10 months ago
162 views
Shared 10 months ago
89 views
What is Jailbreaking, Rooting & Cracking? What are the Security Risks involved? Everything discussed
Shared 10 months ago
135 views
Shared 10 months ago
952 views
Shared 10 months ago
63 views
Different types of hackers - White, Grey, Blue, Black hat & Elite APT hackers 💥Discussed wid example
Shared 10 months ago
429 views
Shared 10 months ago
177 views
Test of Design & Test of Effectiveness 💥 Examples of Failed Internal Controls 🔏 Explained in details
Shared 10 months ago
2K views